RESONATE:
YOUR
SECURITY
LIFECYCLE
MANAGER
IT SECURITY:
Where do you start?
IT security is made up of many facets. Anti-virus software, a network firewall and a mail protection filter have long been common practice in most companies. But even systems that do not seem security-relevant at first glance can become a problem if they are incorrectly configured and the attacker has landed in the network.
To prevent problems, it is therefore essential to „harden“ your existing hardware and software against attacks.
But where and how do you start? Even experienced system administrators can overlook small details in fast-moving IT with frequently changing requirements.
A RED THREAD.
A SECURITY GUIDE.
AN ANALYSIS TOOL.
With RESONATE you keep the overview.
FOR PENTESTERS, ANALYSTS, IT ENTREPRENEURS OR END CUSTOMERS
ANALYSE AND HARDEN IT ENVIRONMENTS
When you analyse your clients‘ IT, you do so dynamically – what works for one client may not work for the next. The path from initial foothold to full-breach is rarely the same, branches out in different directions and may even change over the course of an engagement. Nevertheless, follow a familiar approach to cover all eventualities as efficiently as possible and not miss anything. Even if you are not a dedicated penetration tester, but simply want to assess the security level of a client, you face the same requirement to create traceable test steps with clear results and recommendations for action.
In addition to ready-made catalogues, RESONATE also offers the possibility to create freely definable test catalogues yourself. In this way, you can achieve the same results across customers without having to rewrite and redefine everything each time, and you can proceed with the greatest possible flexibility.
Offering IT services to your customers without paying attention to security is unthinkable nowadays. There is probably no system administrator who does not have „IT security“ in his portfolio. Nevertheless, there are still countless companies that do not think outside the box when it comes to antivirus and firewalls. The attacker, once he gets into the system, is only partially prevented by these protection systems from reading out sensitive data and selling it on the Internet, or from encrypting the entire environment, including the backup, in order to then demand a very expensive ransom.
RESONATE provides clearly defined instructions in the form of test and hardening catalogues to put a stop to the attacker – and at the same time significantly improves the general IT hygiene in the company. IT security is also achieved by tidying up and robustly configuring systems.
You are neither a penetration tester nor an IT service provider, but you take IT security seriously and would like to use RESONATE to increase your resilience against cyber attacks? However, you only have limited time or expertise to use the product fully on your own?
Don’t worry – we are here to help you. Commission us in the form of one of the consulting packages we offer and we will analyse and harden your IT environment for you. Each step is documented by us in RESONATE. This gives you an overview of the current status and progress of the work at all times. Even annually recurring (so-called) re-tests are covered and documented.
THIS IS HOW IT WORKS
THREE STEPS TO MORE SAFETY
TESTING
01
Analyse the environment.
You follow the test instructions in the respective test catalogue to get an inventory of your own IT or your customer’s environment.
FINDINGS
02
Evaluate the results.
You discuss the findings and recommendations for action from step 1 with your team, your IT manager or your customer.
MITIGATIONS
03
Hardening the environment.
They follow the recommendations for action already stored in the system resulting from step 2 to make the IT infrastructure more secure and harden it against attacks and failures.
THAT DISTINGUISHES US
WHY CHOOSE RESONATE?
A vulnerability scanner can find vulnerabilities in hardware and software automatically and selectively – but checking more complex interrelationships or evaluating concepts is not possible and requires manual effort to ask the right people the right questions.
RESONATE is a sophisticated audit and pentest tool to understand and assess the overall IT system.
Security also comes from working with systems that are regularly cleaned up and kept up-to-date. Through the recurring structured processing of inspection catalogues, an already hardened environment is again scrutinised to ensure long-term security. RESONATE provides the necessary overview – where were you a year ago and where are you now?
RESONATE’s databases contain over 20 years of IT experience. The application of the recommendations for action has been tried and tested with a large number of customers and is based on recommendations from internationally respected security experts as well as the manufacturers of the products themselves. Although this information is freely available on the Internet, it has to be compiled, tested and prepared in painstaking work. Users of RESONATE are spared this work!
Do you encounter unexpected problems when applying the test or curing measures? Our experts are there to help you in word and deed. Thanks to our strong international network, a wide range of knowledge and manpower is available.
Features
Resonate inside
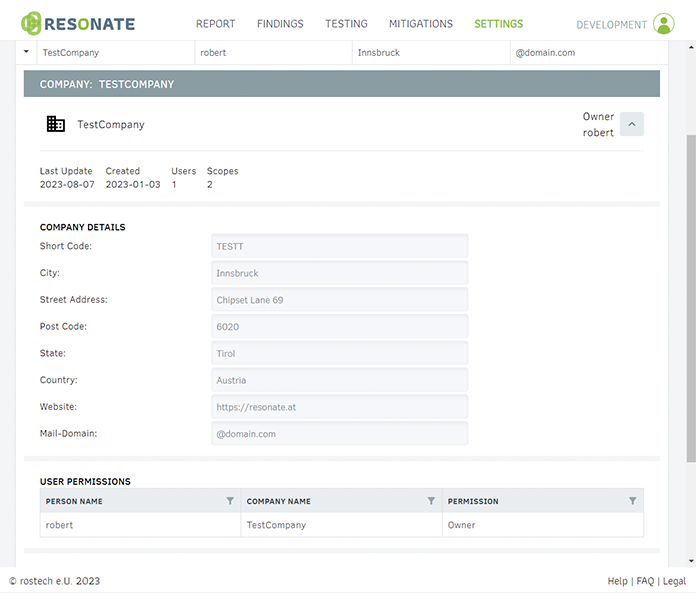
CLIENT MANAGEMENT & AUTHORISATION SYSTEM
RESONATE has a three-tier authorisation system (read, write, own), and only allows those users to view client data who are authorised to do so. Each managed client can be split into additional sub-areas, allowing for special cases such as multiple directory services or multiple locations.
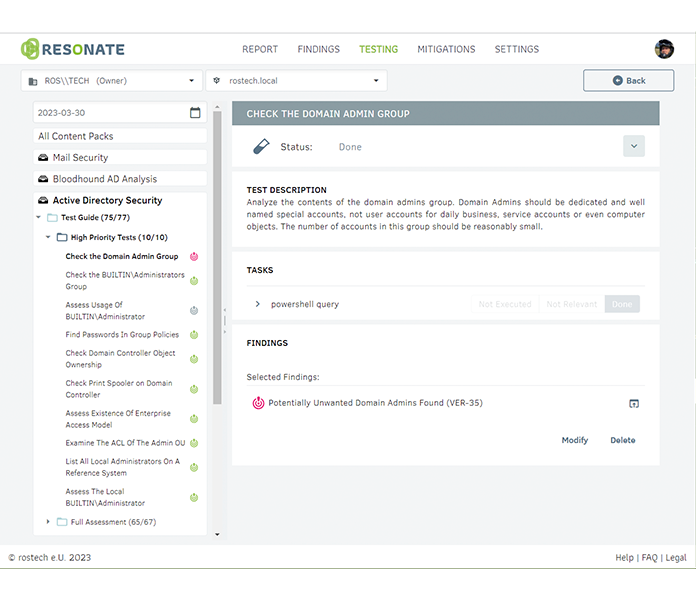
CATALOGUE-GUIDED WORK
RESONATE comes with ready-made data catalogues that you can use to check and secure your infrastructure. In addition, you can create your own catalogues and easily reuse (link) the contents of the system catalogues. A completely freely structurable and nestable folder structure allows unlimited flexibility - for example, you could define a "hardening catalogue light" especially for small customers.
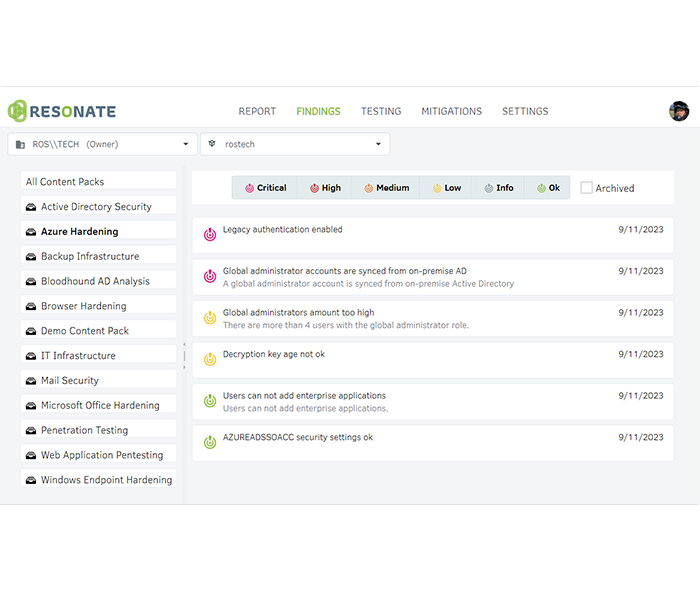
FINDINGS OVERVIEW & REPORTING
All findings and open measures of each client are listed in a central overview. This gives them a quick and uncomplicated statement of the most important next steps for hardening their infrastructure. Simple reports can be generated and sent for special services or reporting to the management.
OUR PACKAGES
PRICES & FEATURES
RESONATE is currently only available for existing customers. If you are interested please send us a message by e-mail to info@resonate.at.
